Patching your Hitch SSL installation for OpenSSL Padding Oracle vulnerability (CVE-2016-2107)
OpenSSL Padding Oracle vulnerability is a high-severity issue due to a memory corruption vulnerability that affects versions prior to April 2015.
Upgrade to 1.0.2c, 1.0.1o or later versions that address this vulnerability.
If you followed my earlier articles on installing and configuring Hitch to terminate SSLs on your DigitalOcean box, here's how you can upgrade to patch the vulnerability.
SSH into your droplet as root and run the following:
openssl version
If your version is older than the two mentioned above, the host is vulnerable. To upgrade, simply run:
yum update openssl
# verify the version installed
openssl version
Once the installation completes, run the following to restart Hitch, to pickup the latest OpenSSL that we just installed:
service hitch restart
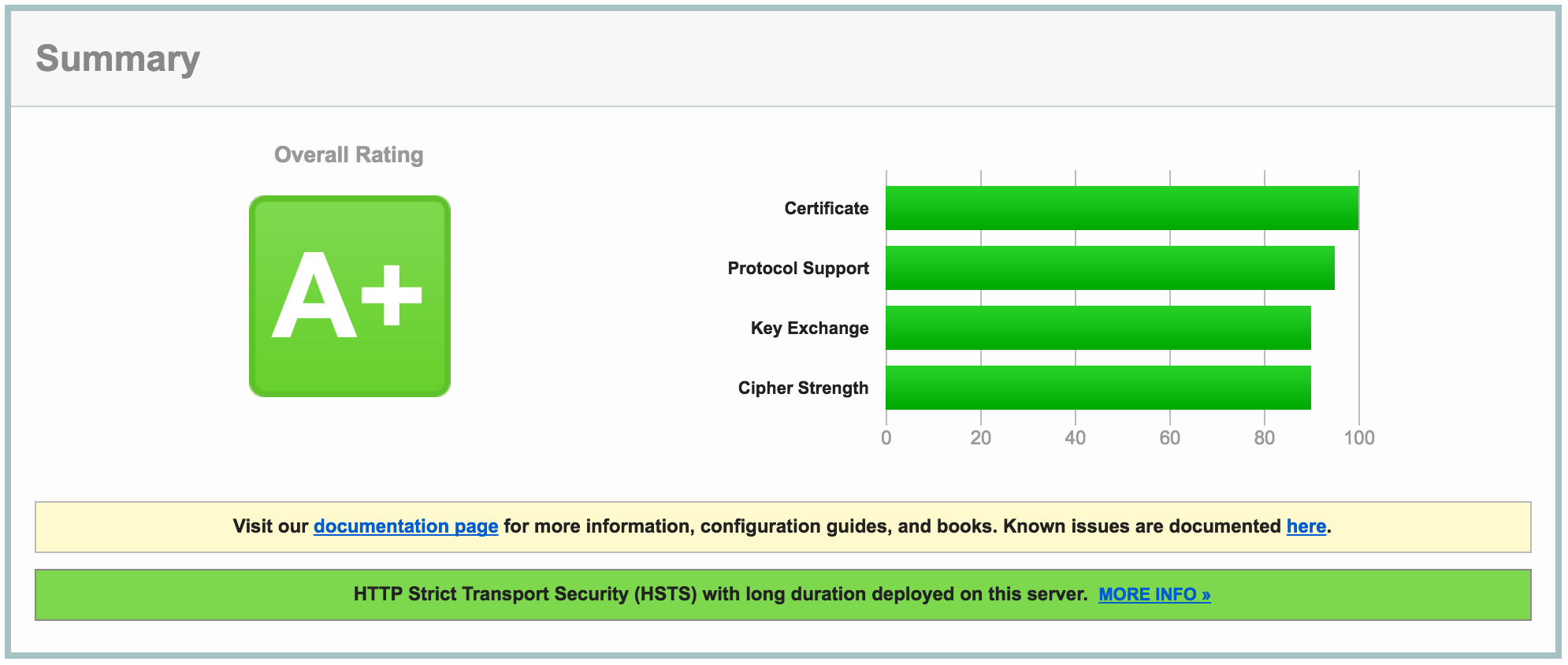
Once Hitch restarts, head to Qualy's SSL Labs to check if your certificate installation is secure.